Single sign-on solution for web applications, mobile and RESTful web services
Keycloak is an authentication server that provide users with the ability to centrally login, logout, register and manage their user accounts. The Keycloak administration UI manages roles and role mappings of any application secured by Keycloak.
The core concept in Keycloak is a Realm. A realm secures and manages security metadata for a set of users and registered clients. Users can be created within a specific realm within the Administration console. Roles (permission types) can be defined at the realm level and you can also set up user role mappings to assign these permissions to specific users
A client is a service that is secured by a realm. You will often use Client for every Application secured by Keycloak. When a user browses an application’s web site, the application can redirect the user agent to the Keycloak Server and request a login. Once a user is logged in, they can visit any other client (application) managed by the realm and not have to re-enter credentials. This also hold true for logging out. Roles can also be defined at the client level and assigned to specific users. Depending on the client type, you may also be able to view and manage user sessions from the administration console.
How security works in Keycloak
Keycloak uses access tokens to secure web invocations. Access tokens contains security metadata specifying the identity of the user as well as the role mappings for that user. The format of these tokens is a Keycloak extension to the JSON WEB TOKKEN specification. Each realm has a private and public key pair which it uses to digitally sign the access token using the JSON WEB SIGNITURE specification. Applications can verify the integrity of the digitally signed access token using the public key of the realm. The protocols used to obtain this token is defined by the OAuth2.0 specification.
Permission scopes
Each client is configured with a set of permission scopes. These are a set of roles that a client is allowed to ask permission for. Access tokens are always granted at the request of a specific client. This also holds true for SSO (single sign-on). As you visit different sites, the application will redirect back to the Keycloak Server via the OAuth 2.0 protocol to obtain an access token specific to that application (client). The role mappings contained within the token are the intersection between the set of user role mappings and the permission scope of the client. So, access tokens are tailor made for each client and contain only the information required for by them.
The Power of social login
The latest statistics on social media for 2015 done by www.statista.com with a staggering total of over 1.4 Billion internet users using social media, make social login and registration more relevant than ever before, Keycloak provides social login allowing the user to register and login using their social media network of choice such as Facebook, Twitter, Google or any other preferred network.
Social login has become very popular in today’s market and almost expected of new applications. It is a faster and much more convenient way for users to register to your application, thus increasing registration numbers. A report called The value of social login done by Janrain in 2013 showed that social login increased registration rates by as much as 50%, the same report also showed that 92% of users report having left a website when they’ve forgotten their username or password, which would not happen had they registered using social media.
Downloading and installing Keycloak
Keycloak can be downloaded from keycloak.jboss.org under the downloads tab.
On the Keycloak website under documentation you can download the 1.2.0.CR1 user guide PDF, this document contains in depth instructions on the different types of installation options available for Keycloak and how to configure the Keycloak server. Here is a link to the Keycloak user guide.
Once you have downloaded and installed the Keycloak server you can follow the youtube tutorial videos created by the keycloak team to set up your web application with Keycloak under the documentation section on the Keycloak web site. These tutorial videos are easy to follow and very comprehensive and appropriate for any audience from someone just starting software development to experts that want to expand their knowledge and learn Keycloak.
Social Login tutorial
Now that you have installed Keycloak and set it up with your application it is time to show you how to set up and enable your users to perform social login.For this tutorial I will use Facebook as the network that users will be able to login with. To enable login with Facebook you first have to create an application in the Facebook Developer Console.
Step 1: Create an application with Facebook.
- Log in to the Facebook Developer Console Click Apps in the menu and select Create a New App. Use any value for Display Name and Category you want, then click the Create App button. Wait for the project to be created (this may take a while). If after creating the app you are not redirected to the app settings, click on Apps in the menu and select the app you created.
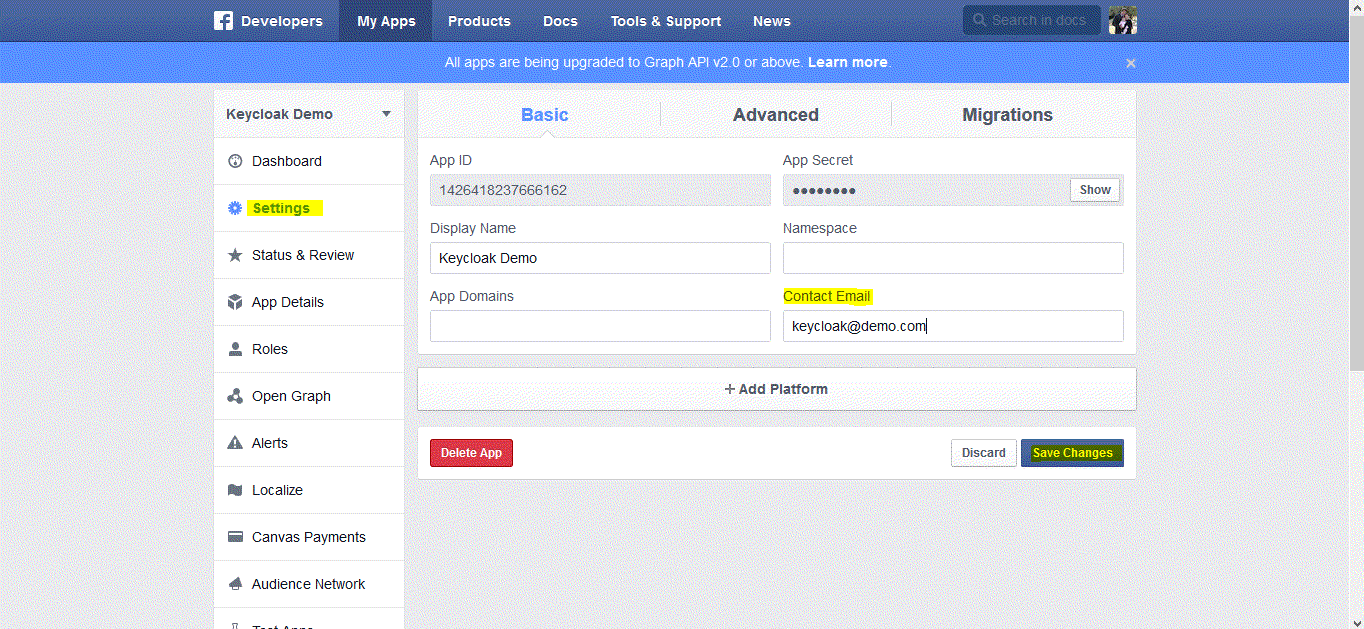
Step two
Step Three
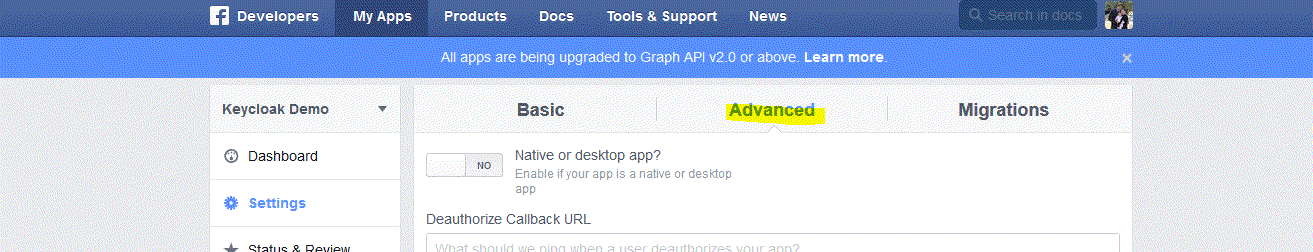
Then click on Advanced. Under Security make sure Client OAuth Login is enabled. Scroll down and click on the Save Changes button.
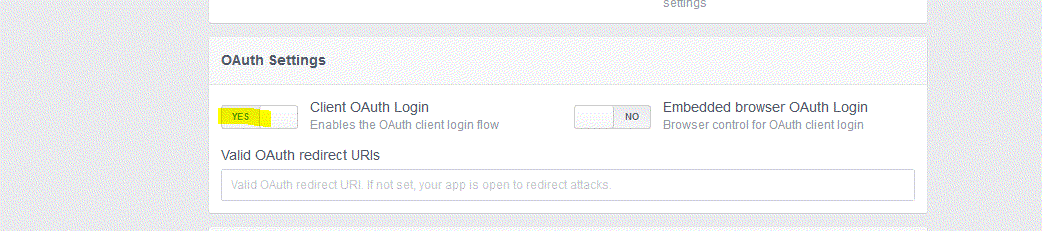
Step Four
Click Status & Review and select YES for Do you want to make this app and all its live features available to the general public? You will not be able to set this until you have provided a contact email in the general settings of this application.
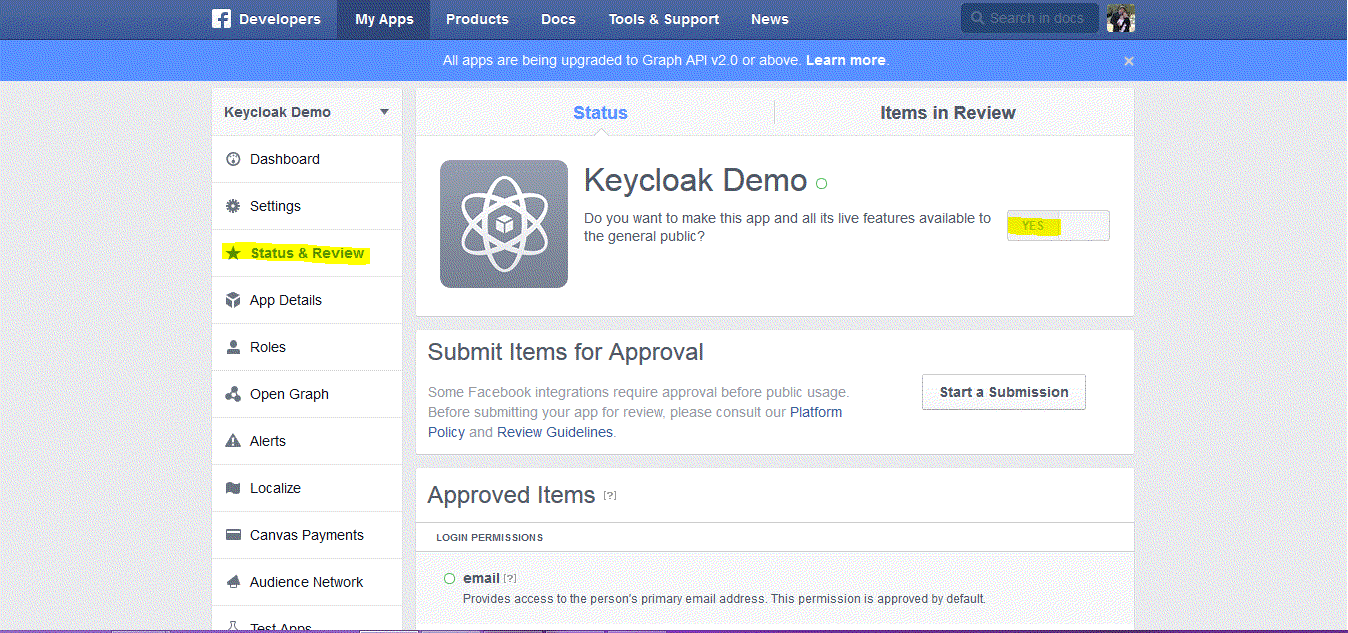
Step Five
Click Dashboard.
Copy App ID and App Secret
(click show)
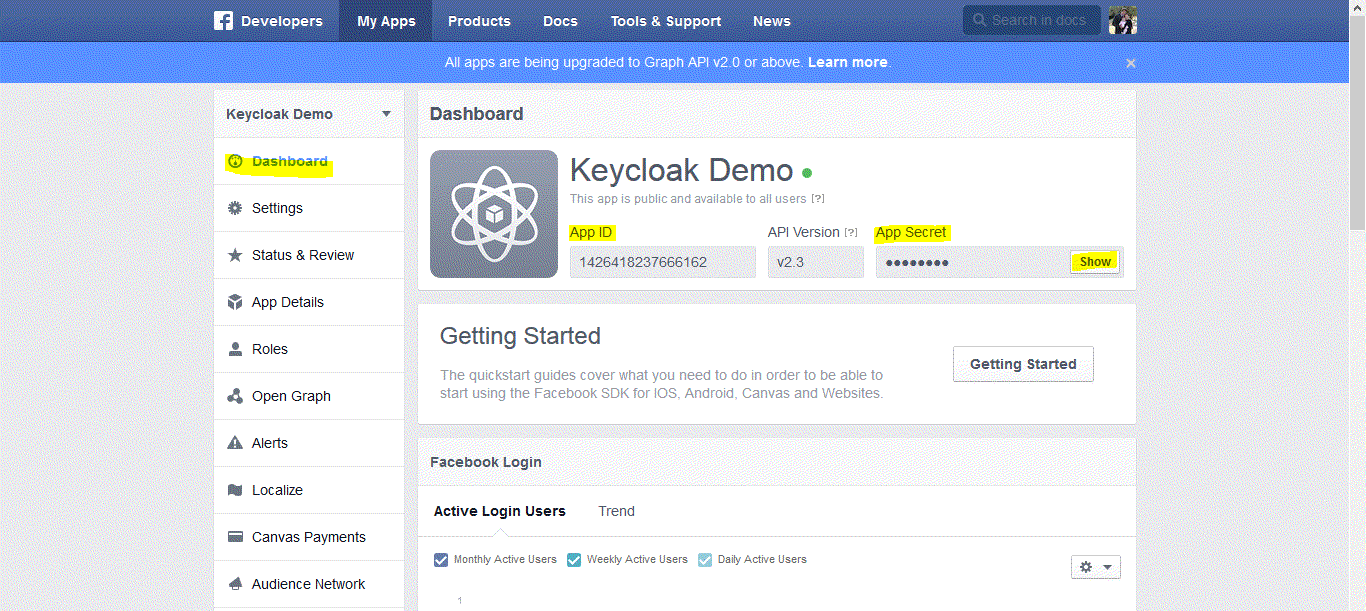
Step Six
Now that you have the client id and secret, you can proceed with the creation of a Facebook Identity Provider in Keycloak.
First make sure that user registration is on, click settings/login.
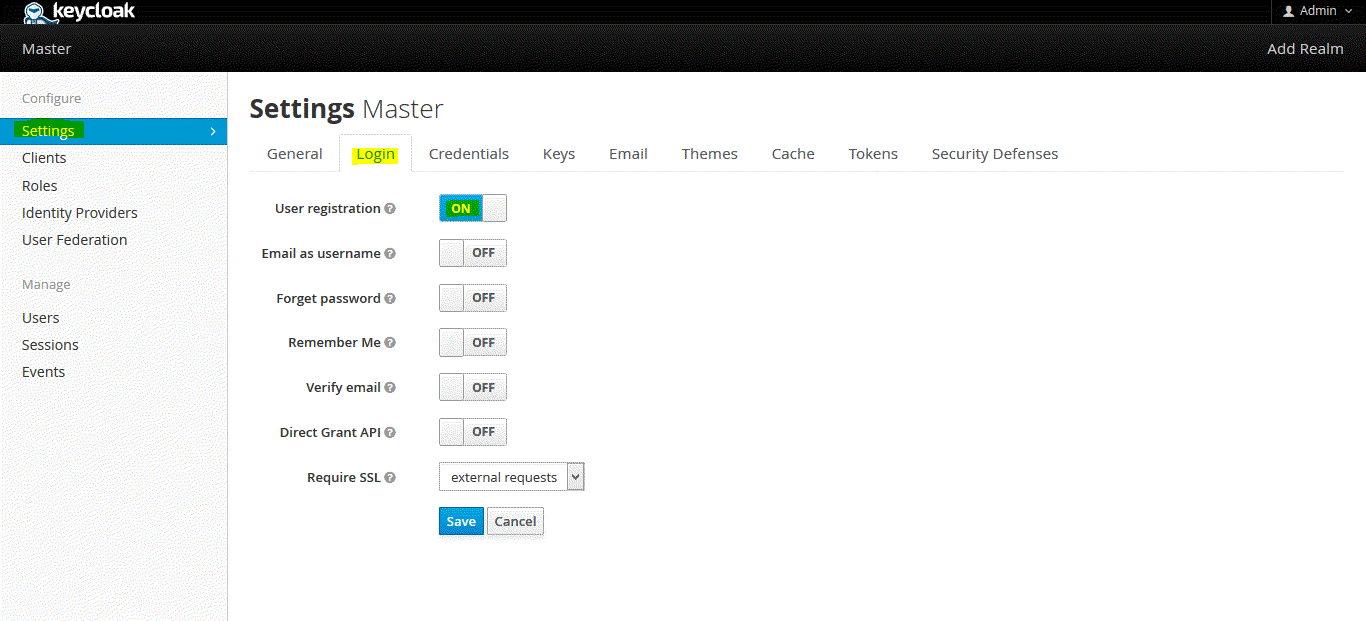
Step Seven
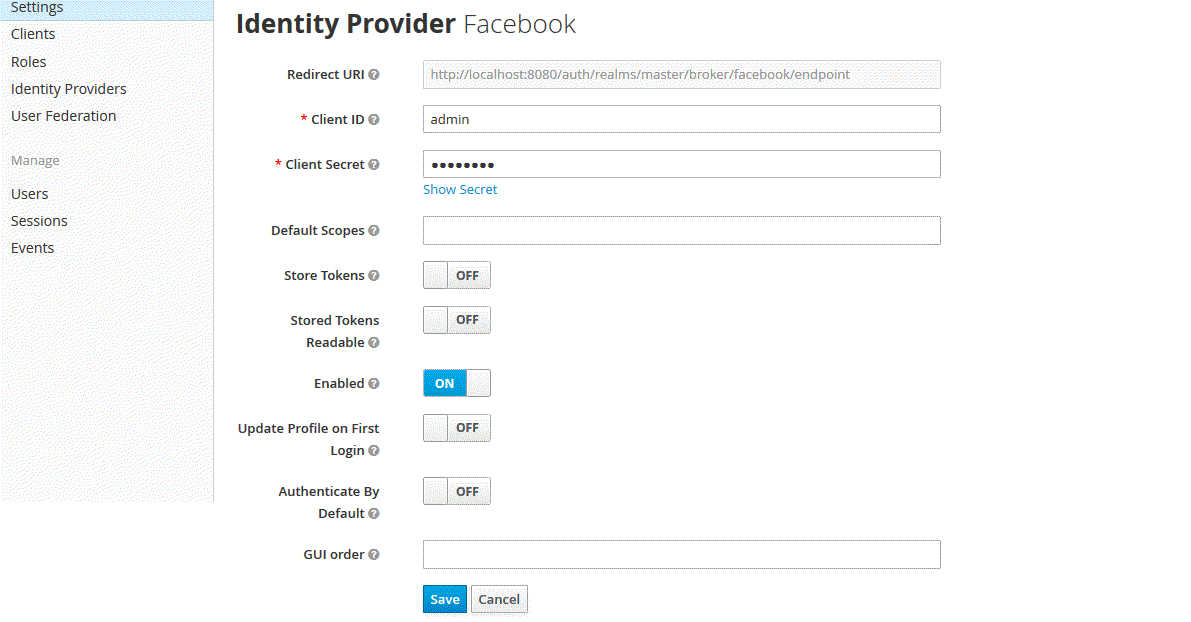
Select the Facebook identity provider from the drop-down box on the top right corner of the identity providers table in Keycloak’s Admin Console. You should be presented with a specific page to configure the selected provided.

Step Eight
Step Nine
Copy the client id and secret from the Facebook developer console to their corresponding fields in the Keycloak Admin Console. Click Save.
>
Step Ten
Once you create the identity provider in Keycloak, you must update your Facebook application with the redirect url that was generated to your identity provider.

Step Eleven
Open the Facebook Developer Console and select your application. Click on Advanced. Under Security make sure Client OAuth Login is enabled. In Valid OAuth redirect URIs insert the redirect uri created by Keycloak. The redirect uri usually have the following format: http://{host}:{port}/auth/realms/{realm}/broker/{provider_alias}

Step Twelve
That is it! Your users can now register and perform a social sign on through Facebook. The Keycloak user guide PDF walks you through how to set up Google, Twitter, LinkedIn, StackOverflow and GitHub in chapter 9 Identity Broker.
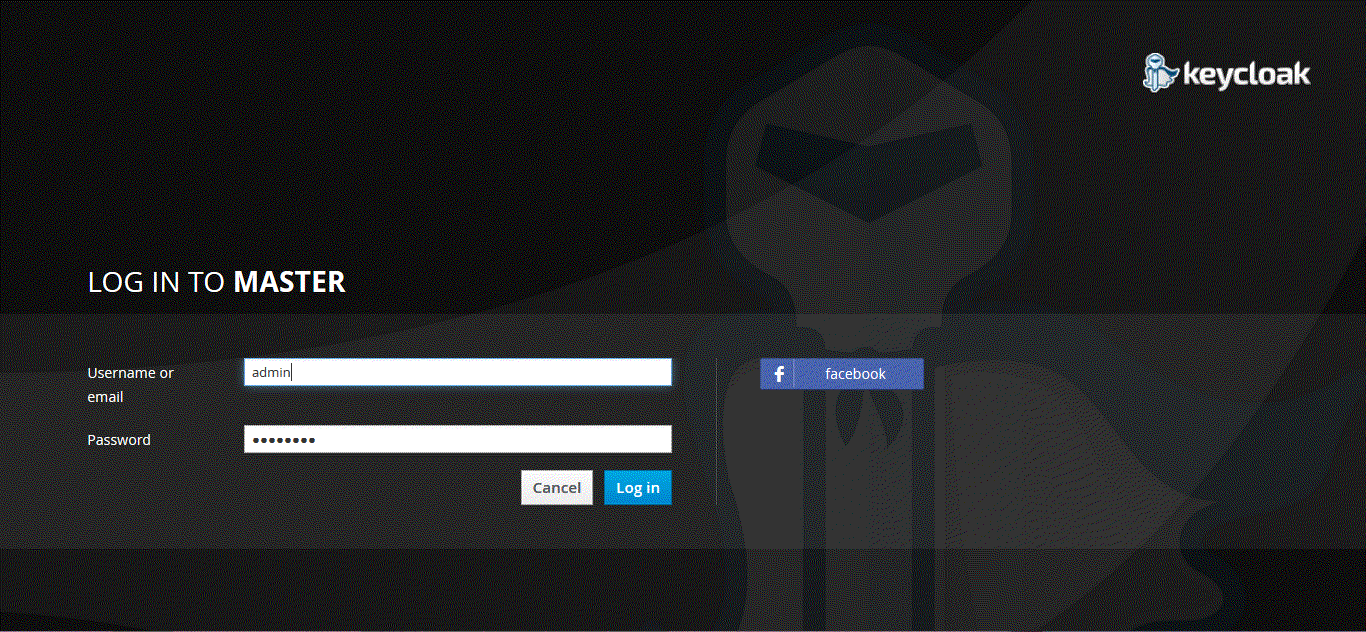
When you logout of the administration console and reopen the console login page you should see the option of registering with Facebook as shown below: